
PT XDR is a product for detecting and responding to cyber threats.
The system refers to information security tools based on a client-server architecture, designed to detect threats on servers and workstations of a corporate network and respond to them. The solution is based on the Positive Technologies product ecosystem and uses unique threat expertise to detect attacks.
1. Unites
Combines events and context from a variety of information security systems, verifies triggers and confirms the fact of an attack.
2. Responsive
Automatically offers options for responding to threats, performs disinfection and allows you to restore the health of systems in the network.
3. Automates
Automates routine processes, prioritizes the queue for analysis, provides the full context of the attack and allows you to find the cause of the compromise.
Product diagram:
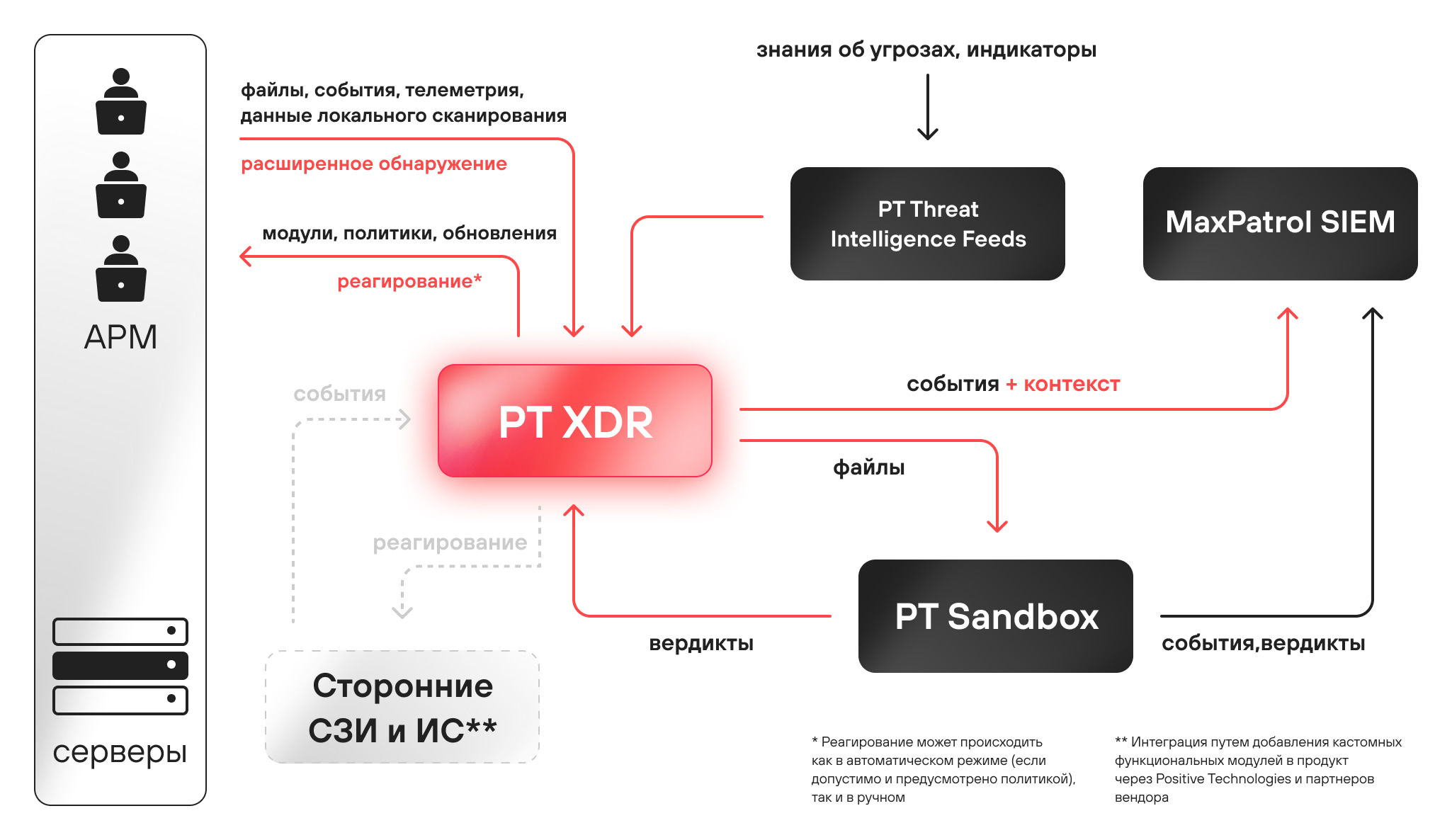
About Positive Technologies
Positive Technologies is a leading global provider of information security solutions. Over 2,300 organizations worldwide use technologies and services developed by our company. Positive Technologies is the first and only company in Russia to go public on the Moscow Exchange (MOEX: POSI).
For 20 years, our mission has been to counter hacker actions before unacceptable damage is done to a business or entire industries.
Our new class of solutions—metaproducts—focuses on the results-oriented approach to cybersecurity. Metaproducts detect and stop attacks in automatic mode with the help of just one person. Positive Technologies’ first metaproduct, MaxPatrol O2, automatically detects and prevents attacks before unacceptable damage is done to the company. MaxPatrol O2 can replace the entire team of a security monitoring center, and it only takes one person to manage it; all in all, this protection system requires minimum knowledge and effort from a specialist.
To demonstrate that the results-oriented approach to information security truly works, we conduct cyberexercises (on our own infrastructure as well as others’) and publicly test our products. Our solutions are based on the research experience and expertise of several hundred information security experts.
